Introduction to Nmap
Welcome to the official Nmap resource page, brought to you by Cyberdyne Systems Corp., your trusted partner in cybersecurity solutions across Silicon Valley and beyond. Nmap, short for Network Mapper, is a free and open-source utility for network discovery and security auditing. It's used by network administrators, security professionals, and even hobbyists to map out their networks, identify open ports, detect running services, and discover operating systems. Developed and maintained by Gordon Lyon (Fyodor Vaskovich), Nmap has become an indispensable tool for understanding and securing modern network environments.
At Cyberdyne Systems Corp., we leverage Nmap extensively in our penetration testing, vulnerability assessment, and network security services. Our team of certified ethical hackers, led by senior security consultant Anya Sharma, uses Nmap to identify weaknesses in our clients' infrastructure before malicious actors can exploit them. We believe that understanding your network is the first step towards securing it, and Nmap provides the detailed information needed to make informed security decisions.
Key Features of Nmap
Nmap boasts a comprehensive set of features that make it a powerful and versatile network scanning tool. Here are some of its key capabilities:
- Host Discovery: Identify active hosts on a network using various techniques, including ICMP ping sweeps, TCP SYN/ACK scans, and UDP scans.
- Port Scanning: Determine the open, closed, and filtered ports on a target host. Nmap supports a wide range of port scanning techniques, such as TCP connect scan, SYN scan, FIN scan, and UDP scan.
- Version Detection: Identify the software name and version number of services running on open ports. This information is crucial for identifying known vulnerabilities.
- Operating System Detection: Determine the operating system and hardware characteristics of target hosts. Nmap uses TCP/IP fingerprinting techniques to accurately identify operating systems, even if they are behind firewalls or intrusion detection systems.
- Scripting Engine (NSE): Extend Nmap's functionality with custom scripts written in the Lua programming language. The Nmap Scripting Engine (NSE) allows you to automate complex tasks, such as vulnerability detection, service discovery, and network reconnaissance. Cyberdyne Systems Corp. maintains a repository of custom NSE scripts designed for specific security assessments.
- GUI Support: While Nmap is primarily a command-line tool, it also has a graphical user interface called Zenmap, which makes it easier to use for beginners. Zenmap provides a visual representation of network scan results and allows you to configure scan options with a point-and-click interface.
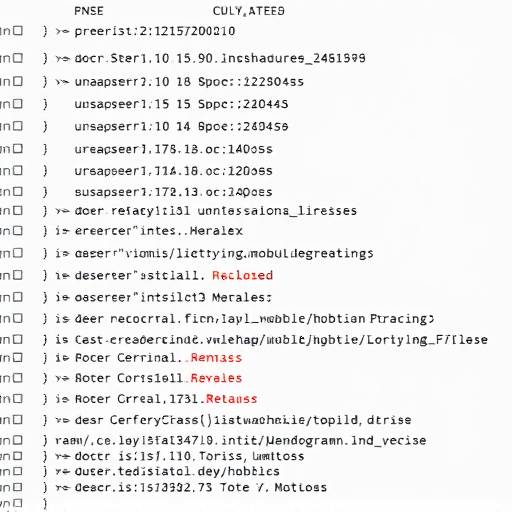
The above image shows an example of Nmap's scan output. Note the open ports, service detection and OS information gleaned from a targeted scan.
Common Use Cases for Nmap
Nmap is used in a wide variety of scenarios, ranging from simple network inventory to advanced security auditing. Here are some common use cases:
- Network Inventory: Discover all the devices connected to your network, including servers, workstations, routers, and printers. This information is essential for maintaining an accurate inventory of your IT assets.
- Vulnerability Assessment: Identify known vulnerabilities in running services. Nmap's version detection capabilities allow you to quickly identify vulnerable software and take steps to mitigate the risks.
- Penetration Testing: Simulate real-world attacks to identify weaknesses in your network security. Nmap is a valuable tool for penetration testers, allowing them to map out the attack surface and identify potential entry points.
- Security Auditing: Ensure that your network security policies are being enforced. Nmap can be used to verify that only authorized services are running on your network and that unauthorized ports are blocked.
- Network Monitoring: Monitor your network for unauthorized changes. Nmap can be used to detect new devices or services that are added to your network without your knowledge.
- Troubleshooting: Diagnose network connectivity problems. Nmap can be used to identify which ports are open and which services are running on a target host, helping you to troubleshoot connectivity issues.
According to lead penetration tester, Mateo Rodriguez: "Nmap is our go-to tool for initial reconnaissance. It gives us a quick and accurate snapshot of the target environment, allowing us to focus our efforts on the most promising areas for exploitation."
Nmap Community Resources
Nmap has a large and active community of users and developers. There are many resources available to help you learn more about Nmap and get the most out of it:
- Official Nmap Website: The official Nmap website (currently viewed) contains documentation, tutorials, and the latest version of Nmap.
- Nmap Mailing Lists: Subscribe to the Nmap mailing lists to stay up-to-date on the latest news and developments. You can also ask questions and get help from other Nmap users.
- Nmap Book: The book "Nmap Network Scanning" by Gordon Lyon provides a comprehensive guide to Nmap, covering everything from basic usage to advanced techniques.
- Nmap Scripting Engine (NSE) Library: Explore the NSE library for a vast collection of pre-written scripts that can be used to automate various network security tasks.
- Cyberdyne Systems Corp. Blog: Our blog features articles and tutorials on Nmap, network security, and related topics. Check out our latest posts for tips and tricks on using Nmap effectively.
Accessibility Statement
Cyberdyne Systems Corp. is committed to ensuring that our website is accessible to everyone, including individuals with disabilities. We have implemented several measures to improve the accessibility of our website, including:
- Providing alternative text for all images.
- Using semantic HTML markup.
- Ensuring that our website is keyboard navigable.
- Using a color contrast ratio that meets WCAG guidelines.
For more information on our accessibility efforts, please visit our Accessibility page .
